Were Capitol rioters a national cybersecurity threat?

- Following the storming of the US Capitol Building, images emerged on social media of compromised government devices
- It demonstrated an unexpected cyberthreat to national security
- Businesses should consider how to mitigate unwanted physical entry onto devices, particularly with remote workforces
Without a doubt, the biggest news item globally this week was that of Pro-Trump rioters forcing entry into the Capitol Building in Washington D.C., in a bid to upset the confirmation of Democrat Joe Biden as the next President of the United States.
Casualties, arrests, and even the discovery of pipe bombs and other weaponry followed in an event that demonstrated the shocking ease with which the institution of the US government can be overpowered physically by an angry mob.
The threat wasn’t just directly physical, however. Rioters also managed to access the computer system in the office of House Speaker Nancy Pelosi, raising concerns about what information and infrastructure could have been accessed by the insurrectionists.
The compromise of the device was publicized on Twitter (in a now-deleted) tweet from the account of Elijah Schaffer, a reporter for right-wing publication The Blaze.
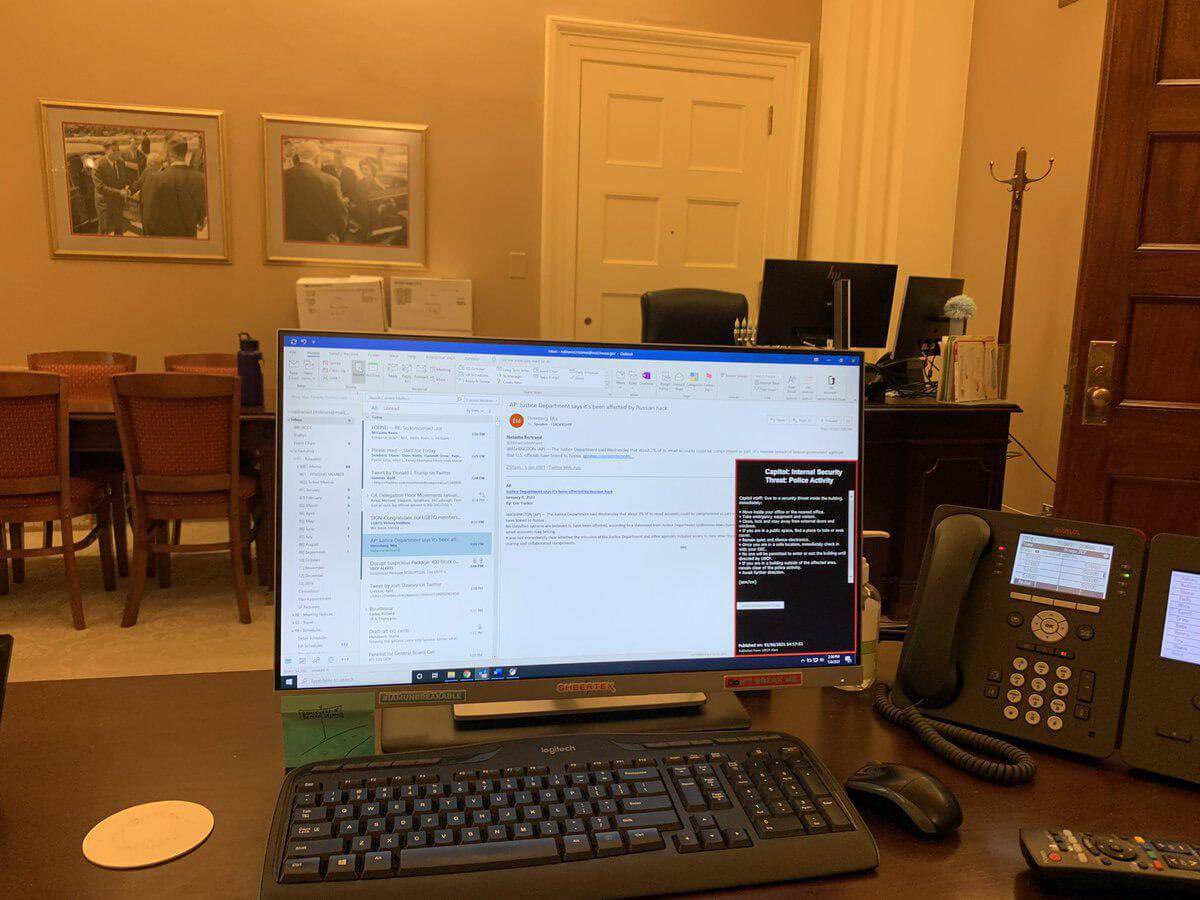
The image original shared by Elijah Schaffer pertaining to be a computer belonging to Nancy Pelosi. Source: K. Brihat
@KBAJBT9 on Twitter
As noted by The Independent, the desktop computer was just one device of what was likely dozens of laptops, phones, and computers hastily abandoned – and potentially left accessible – following the order of lockdown procedures within the Capitol building.
Cybersecurity expert Victor Gevers told the publication that it was a “worst-case scenario” for national cybersecurity, with intruders given the opportunity to plant malicious devices, including bugs, access and copy sensitive information, or upload malware onto machines.
YOU MIGHT LIKE

SolarWinds attacks — a lot worse than first thought?
That’s a particularly real threat, given that rioters had planned and made preparations to invade the building days or more in advance.
“When such a large group of unidentified people has physical access to your unlocked systems and network connections [it] means you can’t trust them anymore. You need to redeploy everything, change credentials, and investigate every[one] that was in that building.
“It also shows the IT department does not enforce an automatic screen lock after a short while of inactivity which is not an advisable thing to do.”
This is Richard Barnett of Gravette, Arkansas posing in Nancy Pelosi’s office. He also posed with stolen mail. He should be arrested immediately. pic.twitter.com/3XfmQbzAVw
— Brad Betts (@870South) January 7, 2021
There is also a risk that images of open email accounts of government officials shared online could open doors for targeted phishing attacks against recipient addresses identified.
This follows the ongoing SolarWinds cyberattack which has seen government agencies compromised after attackers inserted malicious code into a software update for the SolarWind Orion cybersecurity product.
Why it matters for businessess
Ultimately, commentators say the cybersecurity threat to US national cybersecurity following the storming of the Capitol “cannot be overstated”, and IT security within the building leaves as much to be desired as that of the site itself.
For businesses, it’s a stark reminder of how entry points for cyberattacks aren’t always external, and that ensuring measures are in place to protect physical devices from unwanted visitors should be a significant consideration, particularly with employees working from home in unobservable and potentially unsecured environments.
Measures to consider include enforcing automatic lockout after a certain period of inactivity, and consider implementing physical multi-factor authentication devices for access, such as those made by Yubikey.








