Malware is exploiting US election uncertainty

- This year has highlighted how cyber-attackers adopt the theme of the hour — in this case, the US elections
- Events of widespread concern and emotion are optimal psychological angles for social engineering campaigns
- Amid the distractions and trials of 2020, businesses and employees must keep vigilance in their inbox
If we’ve learned anything about cyber-attacks in 2020, it’s that the perfect time to strike is when there’s a big distraction and everyone’s riled up.
The UK’s National Cyber Security Centre revealed that more than 1 in 4 cyber incidents in the past year involved criminals and hostile states exploiting the coronavirus pandemic.
Criminals tried to profit from public fear and distractions. Phishing campaigns were themed from every possible angle, whether purporting to provide public health advice or disguised as Netflix account emails, riding on a spike in use of streaming services during lockdowns.
Right now, of course, the world is watching the results of the US elections trickle in. And with the biggest voter turnout on record and the States’ most controversial President attacking the integrity of the US democratic system, cybercriminals are taking advantage of society’s concerns at an unprecedented time.
On election night, cybersecurity firm Malwarebytes began observing a new spam campaign delivering malicious attachments that exploit doubts about the election process. Operators of the QBot banking Trojan are enticing victims with malicious election interference ballots.
The malicious emails have come as replies to hijacked thread replies, and contain zip attachments aptly named ‘ElectionInterference_[8 to 9 digits].zip’. Once extracted, the document is an Excel spreadsheet that has been crafted as if it were a secure DocuSign file. Users are tricked to allow macros in order to ‘decrypt’ the document.
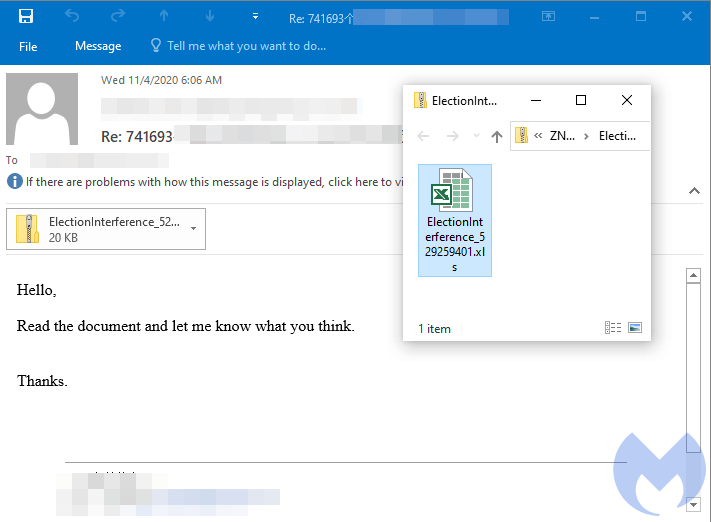
Malicious email with ElectionInterference attachment. Source: Malwarebytes
While the election results are still being evaluated and debated, victims are enticed to open up the document to read about alleged election interference, subsequently downloading malicious payloads onto the victim’s machine.
Once executed, the QBot Trojan will contact its command and control server and request instructions. In addition to stealing and exfiltrating data from its victims, QBot will also start grabbing emails that will later be used as part of the next spam campaigns.
“At the core of the malware attacks we witness each day are typical social engineering schemes,” wrote Malwarebytes. “Threat actors need to get victims to perform a certain set of actions in order to compromise them.
“Spam campaigns routinely abuse email delivery notifications (Fedex, DHL, etc.) or bank alerts to disguise malicious payloads. But world events such as the Covid pandemic or the US elections provide ideal material to craft effective schemes resulting in high infection ratios.”
Once again, and with social engineering attacks at the root of the most devastating cyberattacks, the campaign is a reminder that whatever event has the world’s attention will be seized upon by cyber attackers.










