Global aluminum plants hit by malware attack

As manufacturing companies become increasingly dependent on bringing operations and processes online, they open themselves up to ever greater threats from cyberspace.
Hydro, one of the world’s biggest producers of aluminum, has today (March 19) announced that it has switched to manual operations at its Norwegian smelting facilities amid an ongoing cyber attack.
While information into the nature and damage of the attack is so far scant, Hydro says the attack began on Monday and is ongoing.
Norway’s National Cybersecurity Center (NOR-CERT) believes the malware responsible is LockerGoGa ransomware, combined with an ongoing Active Directory attack. Hydro has yet to confirm this, while the cybersecurity agency has requested information regarding other attacks from its partners.
“The description of the attack from NOR-CERT so far sounds like the attackers manually deployed the malware after gaining access to the networks,” commented AT&T Cybersecurity security researcher, Chris Doman.
Doman added that the take-down of a number of different geographic locations is reminiscent of the kind of damage seen in incidents like NotPetya.
Following the discovery of the attack, Hydro has announced on Facebook that is has “isolated all plants and operations and is switching to manual operations and procedures as far as possible”.
The firm says its main priority is to continue to ensure safe operations and “limit operational and financial impact”, but stresses the attack has not led to any safety-related incidents.
The group, which employs 40,000 staff in 40 countries, has also urged employees in certain areas of the company not to turn on their computers or connect to the network.
LockerGoGa was first brought into the public eye in January after an attack on a French engineering consulting firm Altran. It was reported then that the malware used “brand new code” which couldn’t be detected by robust firewall and data security solutions. Removal of the malware allegedly required a tailored solution.
Following the Altran attack, data security experts at Malwarehunter uploaded a ransom claim that was promoted in an attack with the same virus earlier this year. It’s not known whether Hydro has received a similar claim.
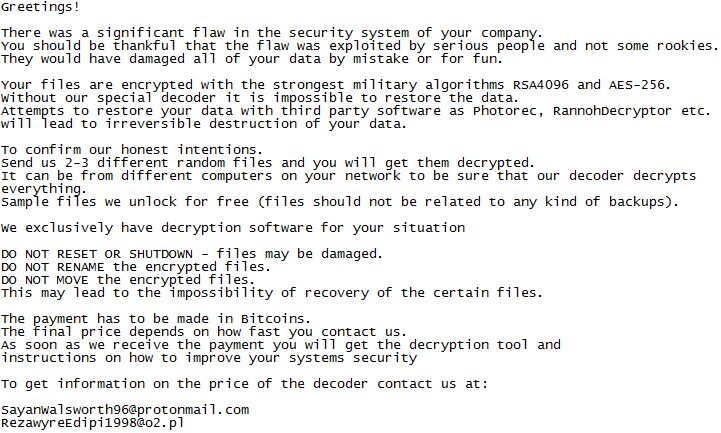
Example of a recent LockerGoGa ransom note. Source: @MalwareHunterTeam/Twitter
“Given they are shutting down operations at some of their plants implies those plants had control system access from the internet or from computers connected to the internet,” said Tim Mackey, senior technical evangelist at Synopsys.
“Minimally, this attack provides a lesson in the value of both network segmentation and ensuring that threat models are created, assuming the threat comes from an internal source.
“With increasingly sophisticated attacks, organizations must assume attackers could compromise internal systems as easily as they might attempt to breach a firewall into a production system,” Mackey added.
“Right now, there’s a lot of missing information on this attack” commented Tim Erlin, VP at Tripwire. “The things we don’t know outweigh the things we do know, and that generally means there will be a lot of speculation.
“This is another reminder to spend the time and money on preparation and prevention,” Erlin added. “If you are an executive at any business, ask yourself what your organization would be doing right now if you were Hydro.”










