Finance CISOs bring fight to cybercrime with threat hunting

The rates of cybercrime are growing fast and, with databases laden with customers’ banking information, financial institutions are often the hottest targets.
According to a report by cybersecurity firm Carbon Black, however, many of these attacks are not simply financially motivated— at least not in the sense of a traditional ‘smash and grab’ heist.
Instead, a growing portion of cybercriminals are prepared to hold organizations to ransom, while others seem set on pure destruction.
Surveying CISO respondents from large financial institutions— including four of the top 10 banks in the world— the report revealed that in the past 12 months, cybercrime activity has become increasingly sophisticated, leveraging new tactics, techniques and procedures (TTPS) to maintain persistence and counter incident response efforts.
“Financial institutions are grappling with some of the most sophisticated cybercrime syndicates,” said Tom Kellermann, the report’s author and Chief Cybersecurity Officer at Carbon Black.
“Perhaps the most concerning indication from this report is the stark increase in destructive attacks, which are rarely conducted for financial gain.”
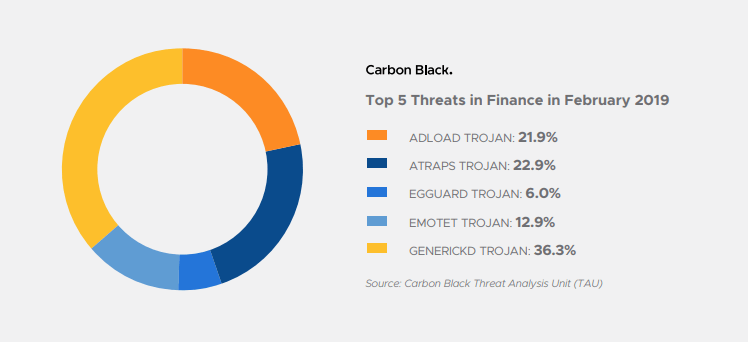
Source: Carbon Black Threat Analysis Unit (TAU)
While two-thirds (67 percent) of financial institutions reported an increase in cyberattacks in the last 12 months, more than one quarter (26 percent) also said their businesses had been targeted by ‘destructive attacks’. That represents an increase of 160 percent since last year.
Carbon Black describes these attacks as being launched with the aim of being “punitive by destroying data”. A recent and notable example is that of VFEmail, which suffered a devastating attack last month, leading to the loss of 18 years’ worth of data.
YOU MIGHT LIKE

Qbot malware resurfaces in new business attacks
In the face of the mounting risks, CISOs are increasingly ‘taking the fight’ to cybercrime; some 47 percent of financial institution security officers are now operating threat hunting teams, an increase of 27 percent on 2018.
Threat hunting consists of the interrogation of a network based on the assumption that it has been breached, and the trend highlights a move away from reactive security as companies can no longer afford to have a cybercriminal “dwell” on their system for months until they are notified by law enforcement.
A recent report by eSecurity Planet found that more than half (51 percent) of organizations— which are more likely to be under heavy regulation, such as in finance and healthcare— were involved in threat hunting once a year or more. However, that number dropped to 40 percent for businesses of 100 employees or fewer.
As demonstrated by Alphabet’s new cloud-based cybersecurity tool, the tactic is becoming increasingly important as attackers become more adept at avoiding detection and move away from “smash-and-grab” attacks to “ongoing siege-based hostage situations”. Twenty-one percent of financial institutions reported experiencing ‘C2 on a sleep cycle’.
“This allows malicious actors to minimize detection by varying their presence, appearing from different locations throughout the network at different times, and disconnecting before their access channels can be fully identified and cut off,” said Kellerman.
Other key findings from the report, include:
# 1 | 32% of surveyed financial institutions encountered “Island hopping’, an attack where supply chains and partners are commandeered to target the primary financial institution.
# 2 | 21% experienced ‘Watering-hole attacks’ during the past year, where institution and bank regulation websites are hijacked and used to pollute visitors’ browsers, exploiting customer trust in banks.
# 3 | 47% reported an increase in wire transfer fraud, exploiting business process gaps in the wire transfer verification process or through social engineering attacks targeting customer service representatives and consumers directly.









