Not just a load of old log files – SIEM and the modern Security Operations Center

The internet wasn’t envisaged or constructed as a secure communications platform.
Its primary purpose meant that it evolved as a way of communicating which could re-route itself if necessary through multiple nodes. And its first users were the high-end academics and military personnel whose gentlemen’s agreement mentality meant that the system’s safeguards comprised, effectively, of a network of mutual trust.
The first security measures placed over the top of networks consisted of perimeter devices like firewalls, and the effective quarantining (or at least separation) of potentially troublesome data in VLANs.
There was a natural progression from these first methods, as successive generations of devices and cybersecurity methods evolved alongside the advances made by hackers; each side in the ongoing war attempting to outwit one another, and steal a march on the other’s next move.
Alongside stateful, packet-inspecting firewalls came intrusion detection systems (IDS), intrusion protection systems (IPS), and endpoint security systems. These are being joined in recent years by algorithms which attempt to analyze behavior patterns in user / entity behavior analytics systems (UEBA).
With UEBA, users’ (both internal to and outside of enterprises) interactions are compared with expected behavioral norms. Therefore, activity in general rather than rule adherence is added to the SOC’s security palette. Of course, any infringements still needed to be flagged with alerts (albeit coming from a different type of source).
Some commentators point to UEBA is a potential powerful cyber defense technology, as the high quantity of data that can be gathered is well suited to machine learning algorithms. The constant analysis may further refine machine definitions of online behavioral norms, and therefore improve overall threat intelligence – time will tell.
As it stands, the variety of security devices, each with sets of rules and flagged events, creates large amounts of data, as records of anomalies, possible threats, non-standard user or entity, and unexpected network activity.
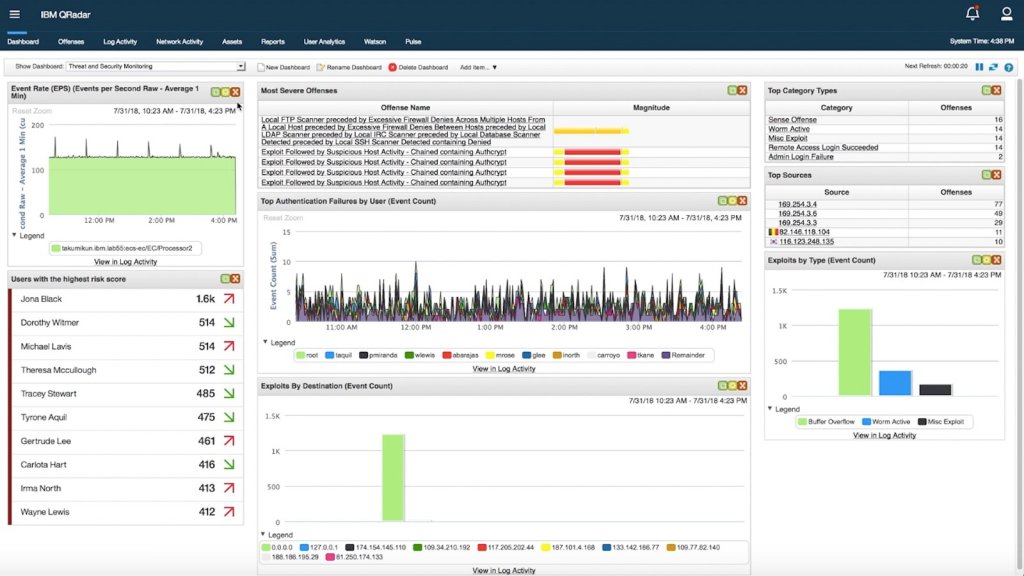
IBM – Qradar
The problems facing security teams aren’t necessarily that bad actor protection measures do not work. Rather, the defenders of the business are just overwhelmed with data. As any visual artist will tell you, too much of the color red in a picture’s palette obscures any danger signs that also happen to be red.
False positives are a problem, naturally, and the process of reconfiguring rules and alert levels becomes nearly as troublesome for SOCs (security operations centers) as manually combing through log files, line by line. As new generations of equipment and software come online, the mix is thickened and made more complicated.
The same vendors supplying defense solutions often supply SIEM systems (security event and information management), which are a sensible answer to the overload. SIEM solutions provide a single point of reference for disparate systems – amalgamating proprietary alert and log formats in one place so that presenting and historical issues stand out significantly.
Three further issues also need flagging:
- The increasing need to satisfy data compliance regulations, such as HIPAA, the California Consumer Protection Act, PCI DSS, and GDPR.
SIEMs now provide interfaces which help audit data practice and point out possible points where non-compliance either is or may be an issue.
- The availability of security intelligence streams, many of which are open-sourced and freely available in standard formats. Additionally, by buying into particular vendors’ infrastructures, there are also often vendor-specific intelligence networks available.
- The somewhat questionable claims made by some (usually persons in marketing roles) that solutions either use artificial intelligence to proactively predict issues before they occur or at least, have some form of machine learning deployment that help security teams comb through the mass of data, by identifying and removing false positives, for example.
- Garbage in, garbage out. Even without the debatable application of “deep-learning”, security teams have their work cut out. SIEMs are only as good as the data fed to them and subject to the accuracy of both their own rulesets and those of the security devices feeding the SIEM. Like examining events in near real-time from a single firewall, being swamped in false positives remains a danger. Conversely, throttling off alert levels can mean significant incidents go unnoticed.
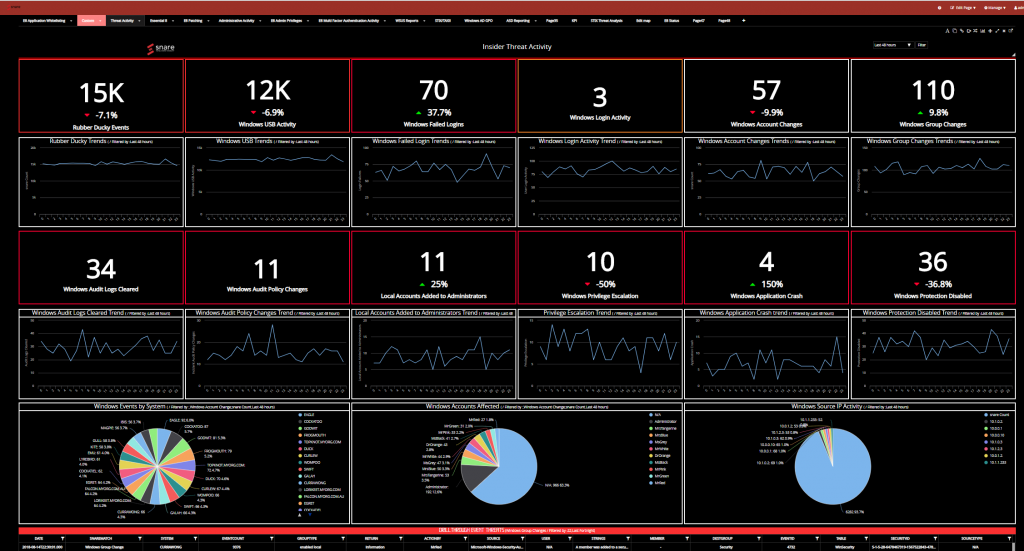
Prophecy International – Snare
At TechHQ we’ve examined two SIEM solutions which we feel warrant your consideration. If you’re considering changing your security management system, or are taking the next step up to automate your existing SOC’s operations, read on. Some aspects we think you might consider:
- Proprietary or open source? The latter requires investment in time to deploy and secure, and also to configure according to particular need. Proprietary systems should come with a level of personalization already included in the purchase price. Advocates of both platform types will debate whose systems are inherently more secure – an argument not entered into here.
- Legacy systems and future topology. New SIEM solutions should be able to work alongside existing SIEM provisions, if they exist, as well as – naturally – be able to take input from all types of security devices. Additionally, can SIEMs be deployed in the cloud, in-house, or both? If your organization is undergoing a digital transformation at present, will the envisaged network topology be covered by the SIEM solution you choose?
- Real-time monitoring. SIEMs traditionally work on logs, but events need correlation in real-time, or in as close to real-time as possible. Many SIEMs now attempt to aggregate flags raised by different systems concerning the same event, in order to cut down on the overall number of alerts that require human intervention.
- Incident response routines. Damage limitation and a fast turnaround in recovery are essential. These start with an organized, pre-defined policy of breach management response, established in advance and followed carefully – modern SIEMs can lead this.
- Privilege misuse. User monitoring is a cornerstone of many types of regulation compliance, as users’ activities are often the weak point in any security plan – especially privileged users. Disgruntled employees’ actions may make the headlines, but simple human error is a more common cause of security concern.
- Threat prioritization. The larger the network presence, the more of a profile is open to attack. When multiple incidents occur, amelioration needs to be prioritized according to business needs. Which systems are mission critical and which are secondary? Can affected systems simply be isolated until resources are available to ameliorate, or is immediate action required?
PROPHECY INTERNATIONAL
Prophecy International’s threat management platform is Snare, which works both with its own Snare Agents and any open source or proprietary security agents. Snare Agents are particularly lightweight, but their use is not mandatory; Prophecy is keen that its solutions can happily sit alongside any existing legacy SOC tech and SIEM.
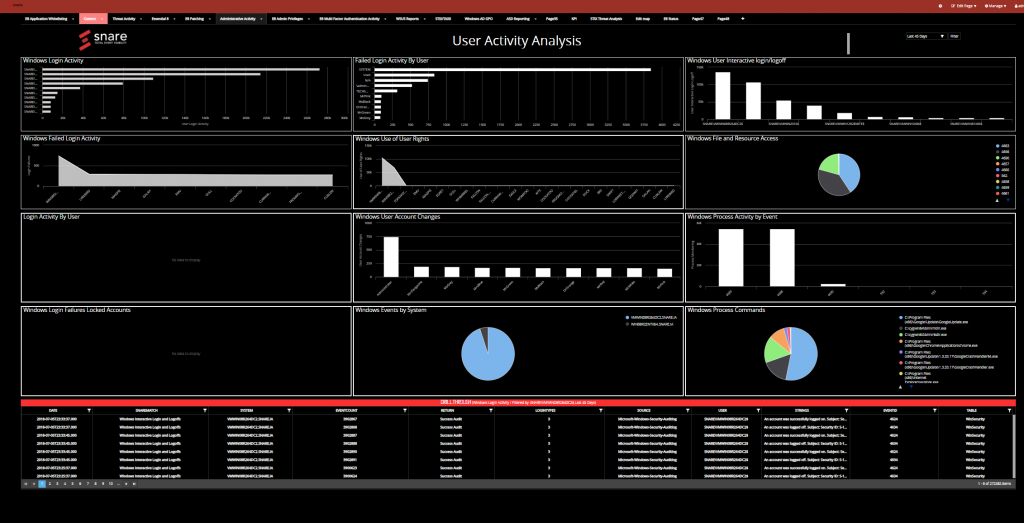
Prophecy International – Snare
Snare Server conglomerates events in real-time and from logs, parsing unlimited data sources. Unlike some of its competitors’ offerings, there’s no “per-log” charging – sources can be added to or dropped at will with no licensing worries or threat of increased costs.
Snare is not, however, a vanilla logfile analysis tool. It allows a proactive security stance to be adopted by SOCs, with real-time threat intelligence created by data aggregation of disparate sources – powerful (and dare we say, even attractive) dashboards can be built on the fly, as can insightful reports.
Snare comes with a massive range of data connectors, and its agnostic architecture means security policies adhere to the organization’s strategy rather than having to conform to the specifications of another vendor’s systems.
Prophecy has placed a great deal of emphasis on ensuring the SIEM drives data compliance according to your geographies making Snare ideal for any business that crosses continents. There are full security accounting routines & reports, and forensic level of data analysis (plus a powerful, lightweight archiving system).
Snare’s SIEM comes as a cloud app or can be installed in-house. It’s lightweight yet feature-rich, and can pull information from an unlimited number of sources right across the enterprise: server room to the HR department, finance function to cloud SaaS apps, via existing SIEMs and legacy security stack.
You can read more about Snare and Prophecy International here.
IBM
IBM’s QRadar Security Information and Event Management solution helps detect and prioritize threats and reduces the impact of incidents – both by minimizing false alerts and by more accurate determination of intrusions or unusual network activity.
QRadar correlates consolidated log events and network flow data from thousands of devices, endpoints & applications, and aggregates events it identifies as related into single alerts. Time to incident analysis and remediation is therefore lowered.
QRadar is available on premises and in a cloud environment, and so perhaps unsurprisingly, can draw from data sources from edge to bare-metal to cloud.
Not only are related activities correlated, but the results can also be prioritized according to how sensitive the area is that might be under attack.
Parsing and normalization of logs from diverse sources (including STIX/TAXII) is a painless process, with out-of-the-box integration to over 450 security solutions commonly found across the enterprise.
The ensuing database of data is highly scalable, self-tuning and essentially self-managing. Both external regulation & compliance requirements, as well as internal policy & reporting needs, are met – plus, for those organizations who don’t wish to invest in their own SOC team, the whole SIEM solution is available as a service from Big Blue.
*Some of the companies featured on this editorial are commercial partners of TechHQ








